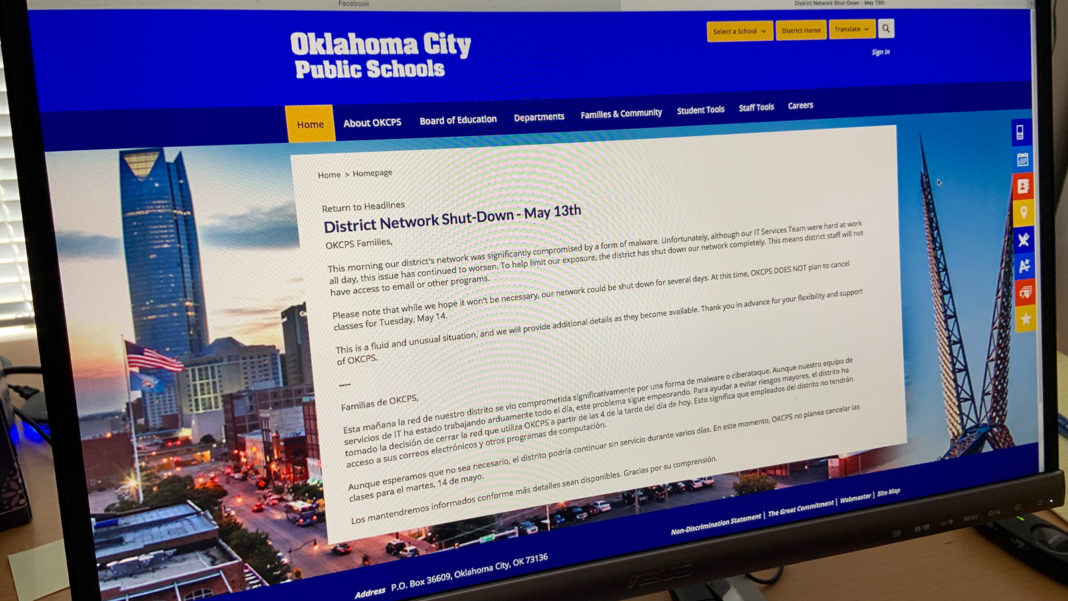
Last Updated on May 21, 2019, 4:47 PM | Published: May 21, 2019
After a full seven days of efforts by district staff and third-party contractors to recover from a crippling ransomware attack, Oklahoma City Public Schools has declared their network to be “fully operational.”
Staff and contractors continued to work over the weekend to clean over 11,000 devices that could have been infected.
Tuesday afternoon, district Media Relations Manager Arely Martin released a one-paragraph statement that praised the efforts of third-party contractors and district IT staff for their efforts.
“Our third-party forensic experts have confirmed that to this point we do not have evidence that any personal, identifiable information for students or staff has been compromised,” Martin’s statement said.
However, in many ransomware and other malware attacks, the only way to confirm if information has been compromised is from evidence or lack thereof in the wild on the Internet months and years later.
The district is the largest in the state with approximately 45,000 students whose identifying information could have been compromised.
The statement mentioned a criminal investigation but gave no details.
Since Monday
The network was taken down at 4 P.M. Monday to isolate the network from the Internet after district IT staff detected a malware attack underway that morning.
Then, Tuesday, at 5:22 p.m., an email was sent to the media that said, in full:
OKCPS continues to address the recent ransomware attack. We are grateful to our staff for their flexibility and for continuing to put students first as our IT Services Teams work with our third-party experts to resolve the issue. OKCPS will provide updates when we have significant progress to report. We appreciate the community’s patience as we respond to this matter.
That was the first time the term “ransomware” was used in a statement by the district.
We asked district spokespersons for information on Wednesday.
Even though we were referred to to the Tuesday email, we ran a report to keep the public aware of the issue. Then, Friday, Free Press asked again for an update in the morning. We ran another story and then updated it late Friday once the district issued a statement.
Free Press then updated our earlier report because the district issued a brief statement at the end of business hours Friday.
It said that their IT staff and third-party “partners” or contractors would continue to work over the weekend to recover the district’s network and get it functional.
Free Press will continue to monitor this situation.
Ransomware
“Ransomware” is a sub-category of the more general term “malware.”
One digital security company, Trend Micro, gives this definition of ransomware on its website.
“Ransomware: A type of malware that prevents or limits users from accessing their system, either by locking the system’s screen or by locking the users’ files unless a ransom is paid.”
In Tuesday’s OKCPS email, the use of the term “third-party experts” is likely a company that is paid to help an organization recover from such an attack.
Two industries have risen as the software and methods of ransomware attacks have become more sophisticated: one that resources the hackers and the other that helps organizations defend against the attacks.
Trend Micro reports that there has been a rise just this month in ransomware attacks “against large corporate networks and workstations in the United States, Canada and parts of Europe.”
The attacks are being made with a new, more powerful ransomware the security industry is calling “MegaCortex.”
Founder, publisher, and editor of Oklahoma City Free Press. Brett continues to contribute reports and photography to this site as he runs the business.