The Oklahoma State Board of Education was the latest to fall victim to a “Zoom-bombing” attack Thursday when a hacker flooded their virtual session’s chat with sexually explicit language.
Zoom is a virtual meeting service widely used for meetings and now many other functions to achieve social distancing while interacting over the Internet. The Board used the service for its meeting Thursday.
This reporter was logged into the meeting to observe.
Even if participants and observers had the chat window closed, when the attack began, repetitive notices in the hundreds streamed at the bottom of the meeting window.
The hack was so obscene that it could not be ignored and the meeting came to a brief halt.
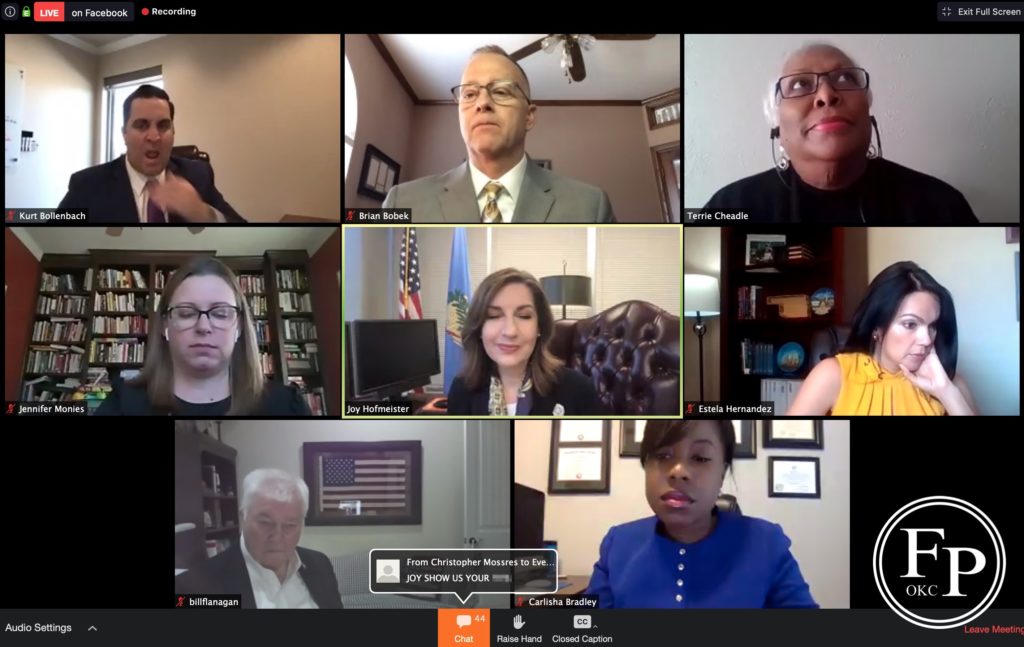
Although State Superintendent Joy Hofmeister herself was the direct target of one of the obscene comments, she kept her composure throughout. The tech assistant eventually spoke up to address the issue.
Some of the members sat motionless during the time, others fidgeted and looked down.
The meeting was paused for around a minute until the chat function was closed to eliminate that vector for the hacker.
But, no doubt, the foul statements were something participants would not be able to unsee.
“Unfortunate realities”
We asked Steffie Corcoran with the OKSDE for a statement about the incident. The response read:
Circumstances none of us could have foreseen have forced the State Department of Education and other agencies and entities to conduct meetings virtually. The kind of incident that happened today is one of the unfortunate realities of doing business in the digital world. We will persevere in our efforts to strengthen security in all platforms used by the agency and will be reporting this hack to Oklahoma CyberCommand.
The Oklahoma CyberCommand is a part of the state Office of Management and Enterprise.
By the end of the day, it was still unclear why well-documented Zoom hacks used even by high school students were not known by a unit in state government called “CyberCommand.”
Known vulnerabilities
In its early days Zoom was used mostly in business circles for remote worker meetings.
But, it is a service that has been questioned by tech security specialists who have been warning about its vulnerabilities for years now.
The hacks were so well known that some businesses refused to allow employees to use the service. Certainly, Zoom is not the only virtual conferencing solution. But, for now, it’s the most widely used so the odds for problems increase.
New users unaware
But, with social distancing during the COVID-19 pandemic, more and more school organizations have quickly turned to the easy-to-use service to at least marginally meet the needs of students nationwide.
There have been notable hacks in other school organizations since the pandemic drove more and more uninitiated users to the easiest service to use, which is Zoom.
Thus, a new, fresh and unaware population was available for hackers – actually malicious pranksters – to interfere in what should be a wholesome enterprise of teaching online.
The problem became so alarming the FBI issued a warning to online classroom users March 30.
Problems baked in
Free Press reached out to security consultant Nathan Sweaney with the company Secure Ideas for information about why Zoom has been having so much security trouble right up to Thursday.
“I don’t know the details about the BOE meeting, but ultimately Zoom is not a great solution for that type of public broadcast,” said Sweaney. “You’re inherently giving access to a wide range of folks that you can’t completely control.”
“But the biggest issue is a core part of their functionality,” said Sweaney.
“By default, the system inherently trusts people that connect to a meeting and allows them to share their camera & audio. The assumption is that you’re meeting with people you know and trust.”
Sweaney said that even last year some users were reporting to Zoom that it was easy to scan their network for meeting IDs without passwords and “Zoom bomb” them.
Password struggles
Zoom gives administrators the ability to set up a password for a meeting but the problem is then distributing the password to those who should have it and keeping it from those who should not especially when some may share it in public forums or even forward an email to the wrong person.
“When you create a new meeting in Zoom, the link they provide to share includes a hashed version of the password,” he explained. “So anyone with that link can get in. Lots of folks have shared that, thinking they weren’t providing the password, when in fact they were.”
There are more complex ways of dealing with security issues using Zoom, like registering users and only allowing access to those users which is cumbersome and fraught with small errors by the users that can stall a meeting.
Also, even if the hosts use a “waiting room” feature where admins can see who has come to the meeting before letting them in, it’s still possible for someone to use someone elses name when they connect.
Brett is the founder, and editor in chief of Oklahoma City Free Press. He continues to contribute reporting and photography to the efforts of the publication as well as leadership in developing support.